Email compromises on the rise
We're seeing a continual increase in the number of compromised email accounts each day, and we've finally identified the source of it. Trend Micro actually wrote more about this source than we could, so you should give their blog post a read: https://www.trendmicro.com/en_us/research/22/l/web3-ipfs-only-used-for-phishing---so-far.html
Though this trend has been a significant one for quite some time, the actual cause of it has escaped us because we've been unable to examine the source of a relevant email until now. Once a recipient has reported an email as spam and we have received it as an abuse complaint (meaning someone is actively complaining to us about this email and sending us a copy to review), we are obligated to view the email. Under any other condition, we would be unable to view such an email as we are limited by our own privacy standards. Our findings in this review were rather troubling.
The phishing email sent by our user was sent by an AWS server, but it was made to look relevant to their industry. The email appeared to be hand crafted by the user, even containing their detailed email signature making it appear as though it was sent from their local computer.
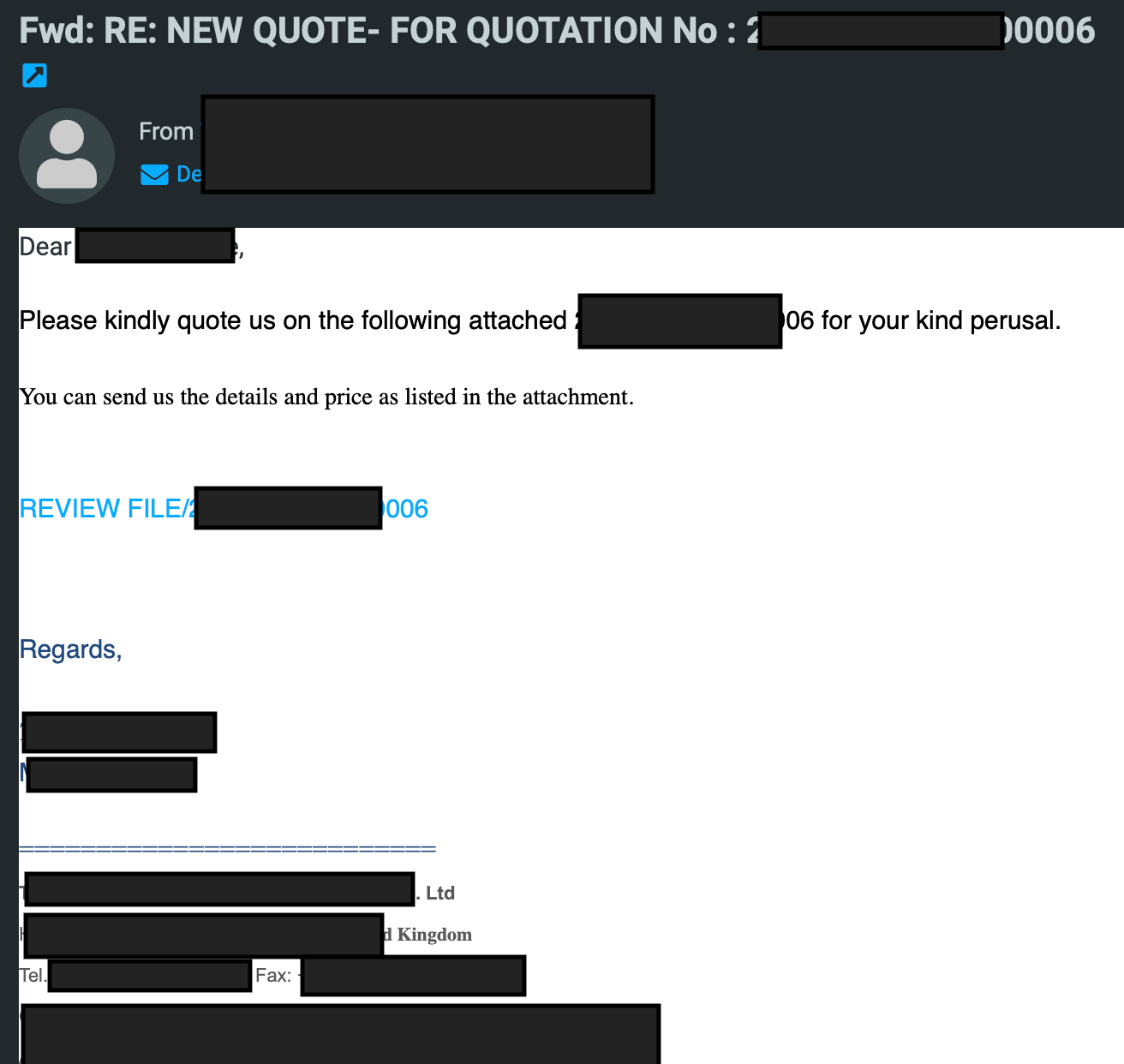
The email contained a link which took the user to an ipfs[.]io link which appeared to contain documents that were of importance, but were hidden behind a login window which required the user to enter their password. On the form, their email account was already listed (as it was added to the URL as a query string), making the user feel even more inclined to just quickly fill in their password to access the documents.
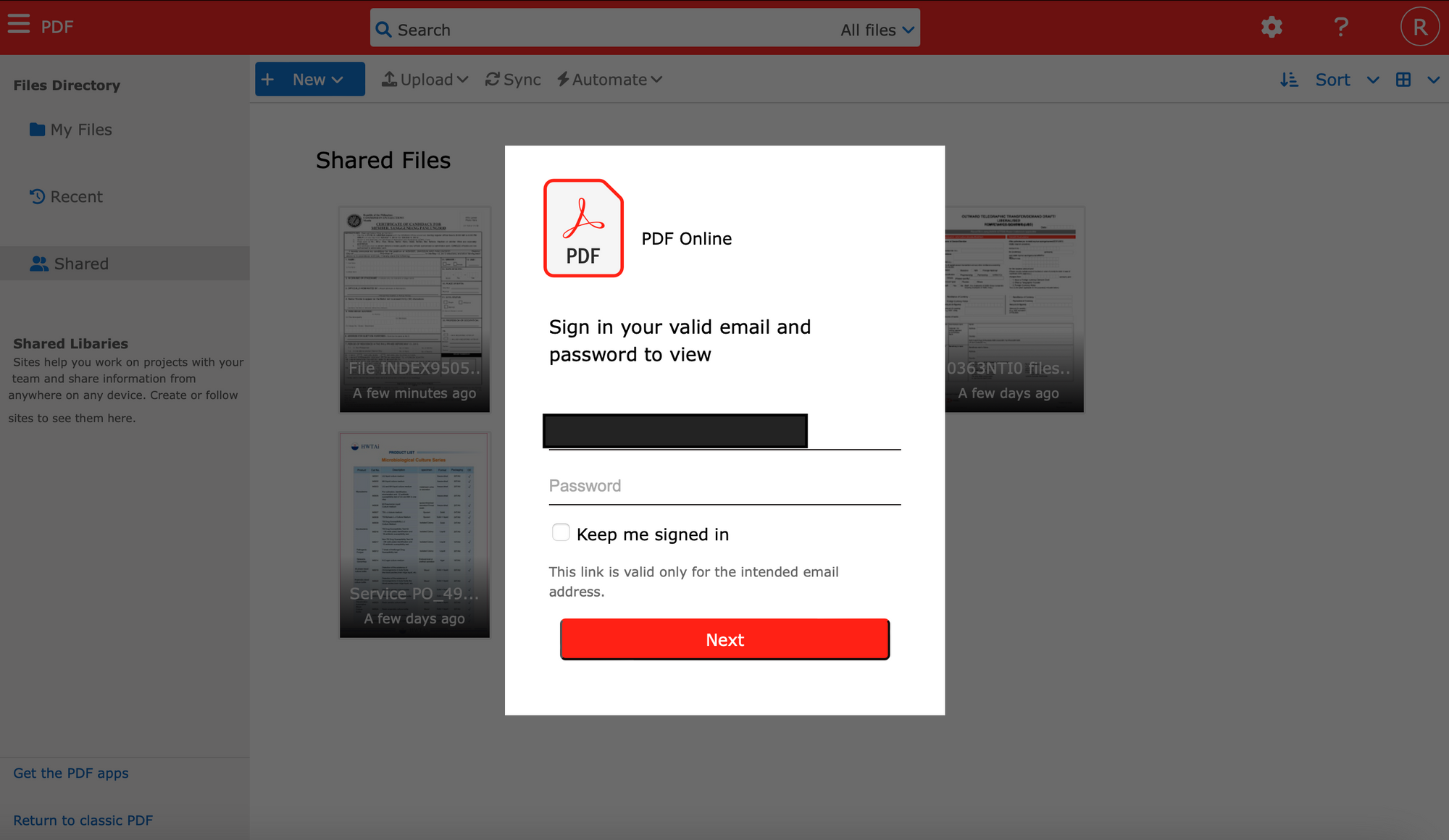
In this case, the user then sent the email to several other users in their office who all trusted it and compromised themselves. This lead to a widespread compromise of their office.
These emails appear in a wealth of forms, and the Trend Micro blog post we linked above does serve to describe several more of them. The point is that there is not just one style of email or form you should be looking out for here. You should never, ever, click a link and then enter your email password. If you believe that the link is sending you to some place that you need to be, go to that website on your own and log into it. Do not trust links that ask for your password, even when they come from people you know.
We have updated our inbound spam filters in a way that we hope reduces these events. However, we expect attackers to change their methods accordingly. You and your users must be educated about this.
Side note: It was a struggle to decide if we should include screenshots and a bit of this user's story. The thing is, this isn't just their story. It's our story. It's a story about how we were alerted in the early morning hours to a wide scale event on our platform. It's a story about how a third party was kind enough to send us a complaint to let us know what bad things were happening on our network. An email sent to us by a third party is data which belongs to us, and in this case it was able to serve a much higher purpose. No personally identifiable information about the customer behind any of these events can be found in this blog post.